- RFID wireless perimeter fence guarding system
- Certification for the highest 4th level of object security
- Direct guidance of PTZ cameras to the place of perimeter breach
- Minimal installation and subsequent maintenance costs
- Lifetime of special batteries up to 8 years in standard operation
Description of the Varya Perimeter system
The Varya Perimeter system enables fence guarding using wireless RFID acceleration detectors that are attached to the fence structure. Varya Perimeter is suitable for all types of standard fences and gates. The detectors communicate with each other by radio in a regular period of 3 seconds on the principle of successive wireless retransmission. FLA RFID detectors detect all fence vibrations and dynamic changes caused by an intruder when climbing over or cutting through the fence, using a 3-axis acceleration sensor. The advantage of the system is the ability to detect detector uninstallation, fence tilting and fence cutting. The installation of the system is very easy and fast, the system is not demanding for maintenance if regular revisions are observed. The batteries in the detectors are replaceable and have a capacity of up to 8 years, with the expected operating life of the detectors being longer compared to the detection cable of "conventional systems". Varya Perimeter allows communication with all types of IAS and with many of the most common types of rotating PTZ cameras. The system accurately guides the rotating cameras to the site of the intrusion online. The outputs of the Varya system can be integrated into superstructure surveillance systems, e.g. using the SNMP-2 protocol.
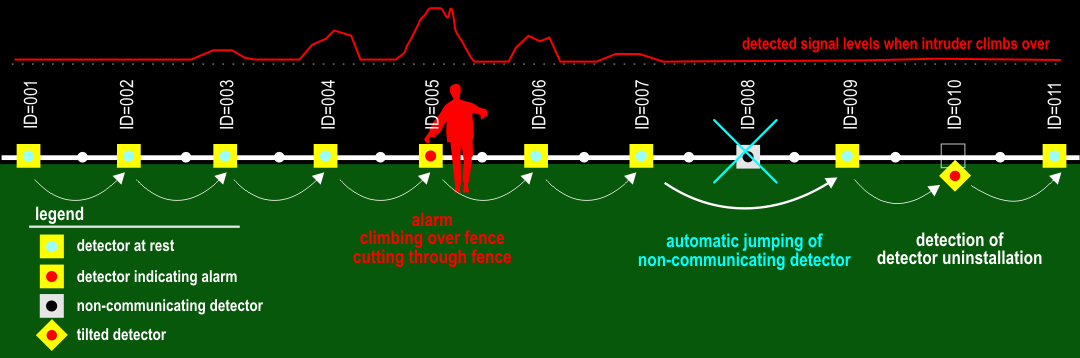
The detectors measure the mechanical quality of the fence automatically. With this measurement, SW calibration of the fence's damaged area can be performed. This intelligence of the system ensures high resistance to weather conditions (wind, rain, hail, etc.). The functionality of all RFID detectors is checked twice a day.
Placement of FLA detectors on different types of fence
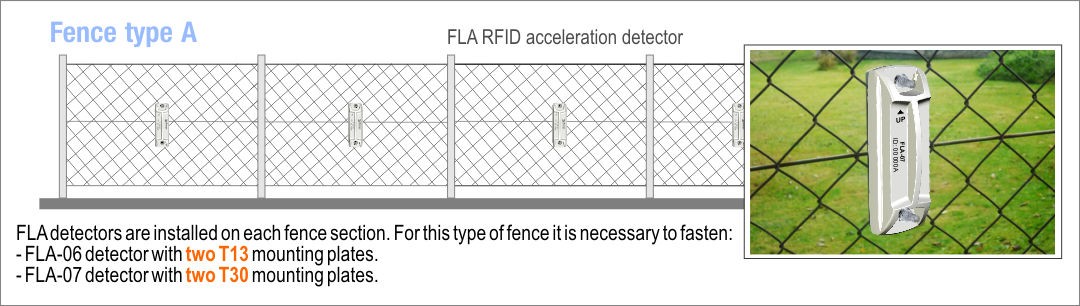
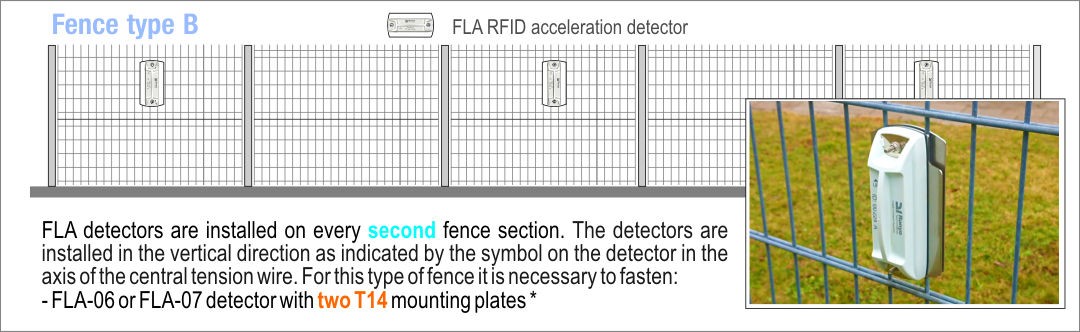
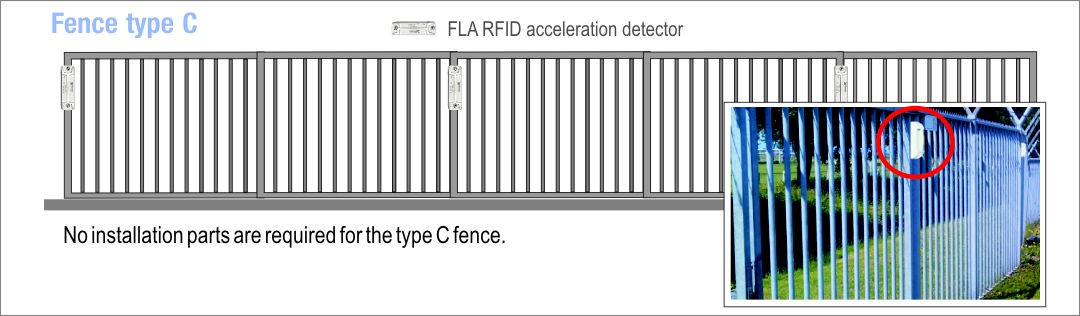
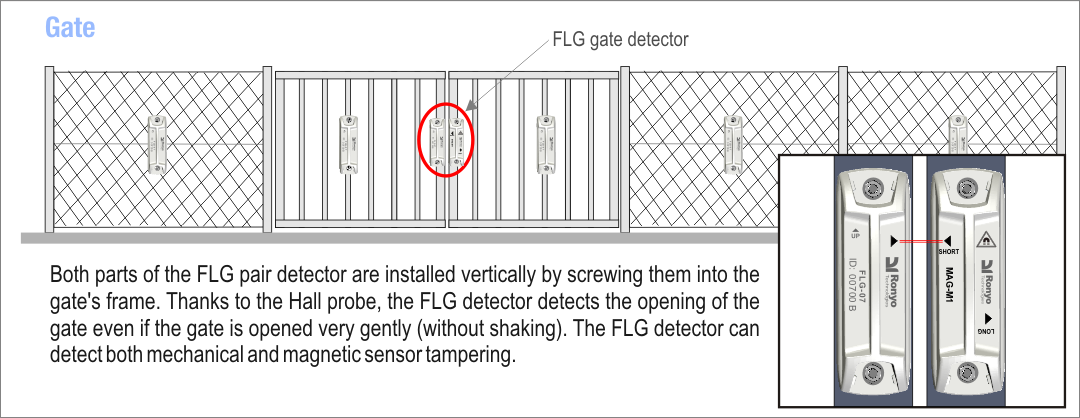
All detectors have a unique ID number. This makes it possible to accurately locate perimeter breaches. The detectors are installed using two gate screws. The detectors are placed on the fence on the inside of the guarded object. Their special design does not enable access to the mounting nuts. Though the detector can detect uninstallation (even in unguarded mode), security nuts with a special key can be ordered for the installation.





